Access Configuration
Once the Web Vision module has been instantiated, the first step is to assign permissions to the roles previously created in the Roles section of WebUI.
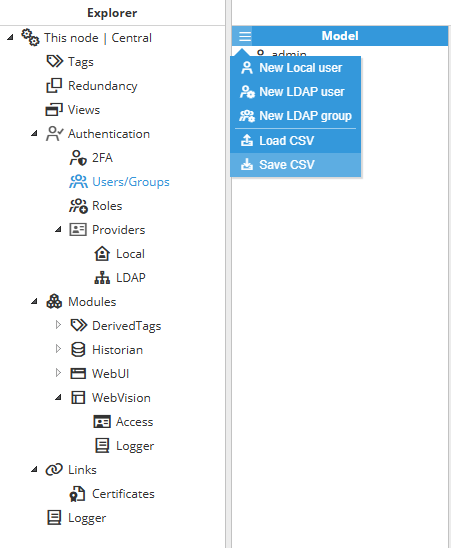
The following options are available for each user:
- Enabled: When set to true, the user is enabled.
- Time zone: User time zone, which is applied to all timestamps shown in the graphical interface. Choose from 4 options:
- UTC (default): All timestamps are shown in UTC.
- User: The time zone is automatically obtained from the system running the web browser.
- Server: The time zone is automatically obtained from the system running Web Vision.
- Custom: Select a specific time zone.
- Permissions: Sets the access level for different parts of the module:
- Designer: Sets permissions for accessing the designer:
- None: User cannot access the designer.
- View: User can view the configuration.
- Edit: User can modify and save configurations.
- Viewer: Sets permissions for accessing the HMI/SCADA application:
- Read: User can access and navigate through the application.
- Write: User can modify tag values and send commands from the HMI.
- Tag access:
- TagFilterPath: Tag filter path access is used to select which tags from the tag model will be available to visualize for the corresponding role.
- Mode: Select whether the filter must include or exclude tags.
- Path: Specifies the path of the tag or group of tags to be filtered.
- Regex pattern: This is a regular expression to filter the tags that will be included. By default, it is set to .*, which means that no filter is applied. Readers can find further information about regular expressions at RegExr.
- Example: If the RegEx pattern is ALARM|WARNING only tags containing ALARM or WARNING in its tag path will be included in the exported file.
- Example: If the RegEx pattern is ALARM|WARNING only tags containing ALARM or WARNING in its tag path will be included in the exported file.
- TagFilterPath: Tag filter path access is used to select which tags from the tag model will be available to visualize for the corresponding role.
- Designer: Sets permissions for accessing the designer:
Module Configuration
The next step is to configure the main Web Vision options: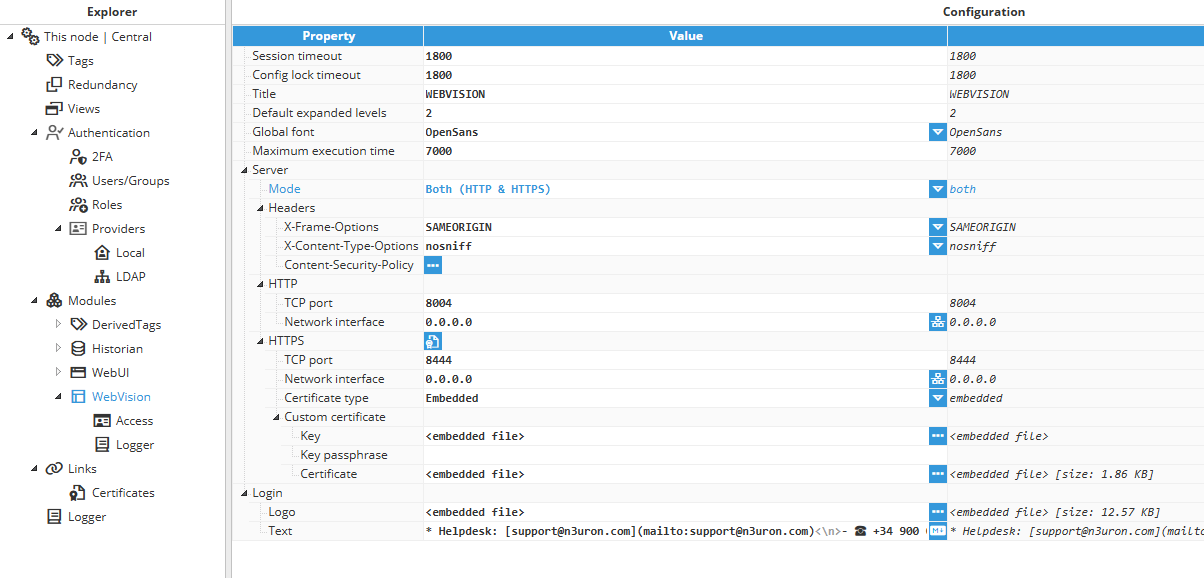
- Session timeout (seconds): Time of inactivity or offline status that needs to elapse before considering the session concluded.
- Inactivity: User sessions will expire after this period of inactivity. A value of “0” disables the inactivity check so that the session will never be closed due to inactivity.
- Offline: When the connection between the Web Vision server and the web browser is interrupted, the session data will be retained in the memory for reconnection. Session data is erased after the Session timeout period elapses. “0“ sets a default timeout of 12 hours to avoid memory leaks.
- Config lock timeout (seconds): Time the user can maintain a configuration locked without making modifications. This lock is automatically released when the user's session expires.Note
A lock is also released when the user session expires. This means that if the Lock timeout is greater than the Session timeout, the lock may be released because of session expiration instead of lock expiration. - Title: The name displayed in the web browser tab for project identification.
- Default expanded levels: Specifies the depth of expanded levels for tag picker controls when opened for the first time.
- Global font: Default font applied to visual components.
- Maximum execution time: Maximum execution time for expressions and functions before the executing script is automatically stopped to avoid infinite loops. This value is expressed in milliseconds.
- Server:
- Mode: Web Vision supports traditional non-secure HTTP connections and secure HTTPS connections.
- Headers: HTTP security headers are additional directives sent by a web server to enhance security by mitigating various types of attacks and vulnerabilities.Note:This feature is available from N3uron version 1.21.9.
- X-Frame-Options: This header determines whether your webpage can be displayed within a frame, iframe, embed, or object tags in other websites.Note:The Content-Security Policy (CSP) HTTP header includes a frame-ancestors directive, making it obsolete for modern browsers; however, it's maintained for backward compatibility purposes
- SAMEORIGIN: Only allows the page to be displayed in a frame on the same origin as the page itself.
- DENY: Prevents the page from being displayed in a frame, regardless of the origin.
- Custom value / =<expressions..>: Users can input their own text. For example, the deprecated "ALLOW-FROM origin" directive, which is ignored by modern browsers.
- X-Content-Type-Options: This header prevents the browser from interpreting files with a MIME type different from the one specified by the server. It’s a measure to stop MIME type sniffing attacks.
- nosniff: Instructs the browser to follow the MIME types provided and not alter them.
Content Security Policy (CSP): It is a robust layer of security that helps to detect and mitigate certain types of attacks, such as Cross-Site Scripting (XSS) and data injection attacks.
- Directive:
- frame-ancestors: Specifies valid parents that may embed a page.
- report-uri: Instructs the browser where to send reports if the content violates the policy.
- report-to: Sets a reporting group for sending violation reports.
- upgrade-insecure-requests: Forces the browser to use HTTPS instead of HTTP when possible.
- Custom value / =<expressions..>: Users can input their own text. For example, "block-all-mixed-content" directive, which prevents loading of insecure resources on a secure webpage, such as loading HTTP content on an HTTPS page, to enhance security and prevent mixed content vulnerabilities.
- Value:
- none: Won't allow loading of any resources.
- self: Only allow resources from the current origin.
- strict-dynamic: Applies a nonce or hash to script elements, granting trust to a script on the page and extending this trust to the scripts it loads, enhancing security by ensuring only trusted scripts execute.
- report-sample: Requires the inclusion of a sample of the violating code within the violation report, ensuring that the specific code causing the violation is included for analysis and remediation.
- inline-speculation-rules: Allows the inclusion of speculation rules in scripts.
- Custom value / =<expressions..>: Users can input their own text. For example, in the "frame-ancestors" directive, the value "*.n3uron.com" can be used to permit embedding of the page within any webpage under the n3uron.com domain.
- Directive:
- X-Frame-Options: This header determines whether your webpage can be displayed within a frame, iframe, embed, or object tags in other websites.
- HTTP:
- TCP port: This parameter specifies the port number to open the web interface. The valid range is 1 to 65535. The default setting is 8004.Note:Please make sure the port is not used by any other application running on the same machine.
- Network interface: Specifies the interface through which the module will be accessible via HTTP. All interfaces are configured by default (0.0.0.0). The option to browse and discover a network interface is also available by clicking on the button to the right.
- TCP port: This parameter specifies the port number to open the web interface. The valid range is 1 to 65535. The default setting is 8004.
- HTTPS:
- TCP port: This parameter specifies the HTTPS port number for opening the web interface. The valid range is 1 to 65535. The default setting is 8444. Note:Please make sure the port is not used by any other application in the same machine.
- Network interface: Specifies the interface through which the module will be accessible via HTTPS. All interfaces are configured by default (0.0.0.0). The option to browse and discover a network interface is also available by clicking on the button to the right.
- Certificate helper: Facilitates establishing HTTPS connections with custom self-signed certificates, offering control over the certificate generation process.Note:This feature is available from N3uron version 1.21.9
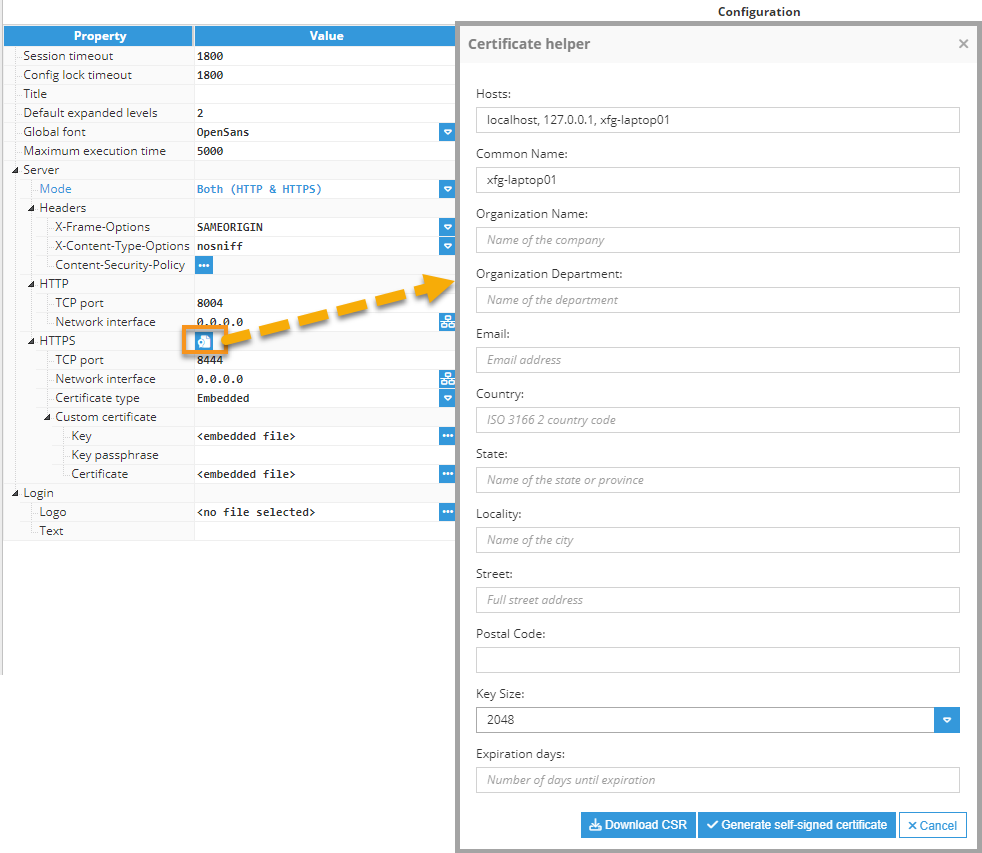
- TCP port: This parameter specifies the HTTPS port number for opening the web interface. The valid range is 1 to 65535. The default setting is 8444.
To open the self-signed Certificate helper, right-click on the icon next to the HTTPS title section, and then fill out the form.
- Hosts: This field in the CSR (Certificate Signing Request) form is used to specify the Subject Alternative Names (SANs) for the certificate. This field allows you to include multiple domain names, IP addresses, and other identifiers that the certificate should cover. The identifiers must be separated by commas.Note:This feature is available from N3uron version 1.21.10.
- Common Name: The fully qualified domain name (FQDN) for which the certificate is being requested. This is typically the domain name of the server where the certificate will be installed (e.g., www.example.com).
- Organization Name: The legal name of the organization or company that is requesting the certificate.
- Organization Department: The specific department or division within the organization that is requesting the certificate.
- Email: The email address associated with the organization or individual requesting the certificate.
- Country: The two-letter ISO code representing the country where the organization is located (e.g., US for United States, CA for Canada, ES for Spain).
- State: The full name or abbreviation of the state or province where the organization is located.
- Locality: The city or locality where the organization is located.
- Street: The street address of the organization's physical location.
- Postal Code: The postal or ZIP code of the organization's location.
- Key Size: The size of the cryptographic key pair to be generated for the certificate, measured in bits. Common key sizes include 2048 bits or 4096 bits.
- Expiration Days: The number of days until the certificate expires. This determines the validity period of the certificate before it needs to be renewed.
When filling out the form to generate the CSR, ensure that all information provided is accurate and matches the organization's official details. This information will be embedded in the CSR and subsequently used to issue the SSL/TLS certificate.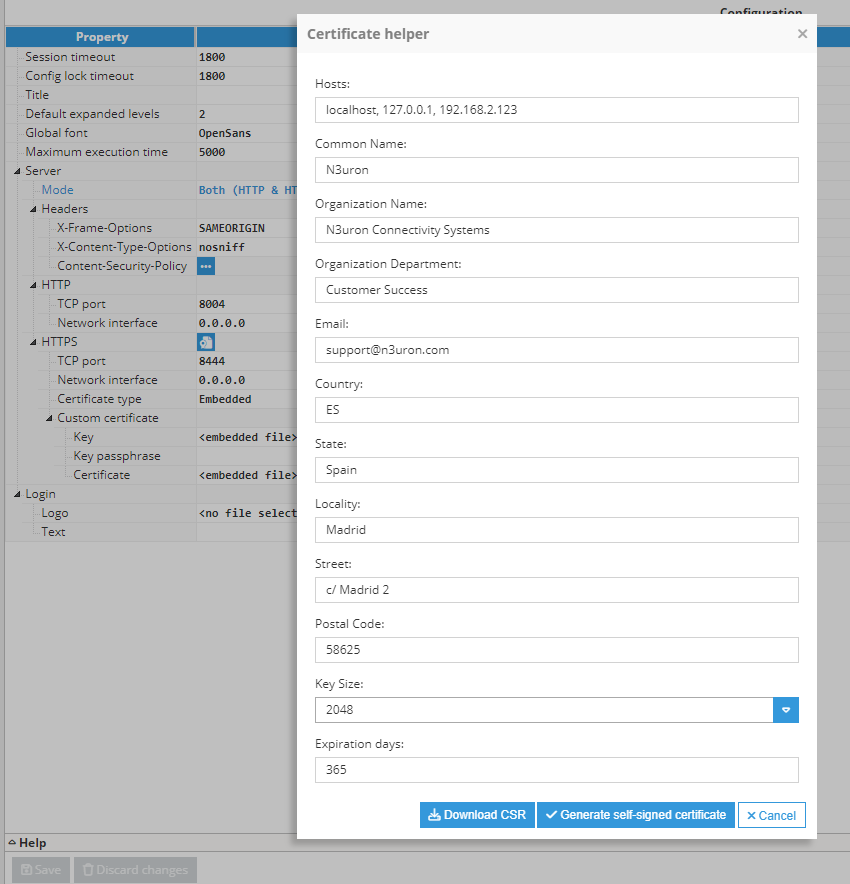
- Certificate type: Selects the server HTTPS certificate:
- Self-signed: The server will automatically create and sign a certificate using an internal certification authority, which can be downloaded by clicking on the ellipsis button on the right side of the Self-signed certificate field, as shown below:
Note Starting from N3uron version 1.21.9, the generation of self-signed certificates has been relocated to the Certificate helper.This certification authority is valid for all module instances and must be imported into all the system/web clients that will be used to access WebUI via HTTPS.
- Embedded: Users are required to provide both the key and certificate files.Note:This feature is available from N3uron version 1.21.7.The key for the embedded certificate files will be secure and cannot be downloaded.
- Custom certificate:
- Key: Private key certificate file used for secure connections. The file must be in .pem format.
- Key passphrase: Enter the passphrase associated with the certificate if it was generated with one; otherwise, leave this field empty.
- Certificate: Certificate file used for secure connections. The file should must be in .pem format.
- File Path:
- Users must specify the paths for both the Key and Certificate files, relative to the data/<instance name>/cert folder.
- Reload Interval: Specify the interval in seconds for reloading the certificate if changes are detected. Set this field to 0 to disable.
- This option is particularly suitable for scenarios involving automatic certificate renewal processes.
- Custom certificate:
- Self-signed: The server will automatically create and sign a certificate using an internal certification authority, which can be downloaded by clicking on the ellipsis button on the right side of the Self-signed certificate field, as shown below:
- Self signed certificate:
- Certified hosts: Comma-separated host list (domains/host names and/or IPs) that will be included in the autogenerated SSL certificate. It is important to include all the hosts from the machine where the WebUI will be accessed so that the web client does not return any errors. Hosts 127.0.0.1, localhost, and system hostname will automatically be added to the certificate.
Note Starting from N3uron version 1.21.9, specifying certified hosts is no longer necessary.
- Certified hosts: Comma-separated host list (domains/host names and/or IPs) that will be included in the autogenerated SSL certificate. It is important to include all the hosts from the machine where the WebUI will be accessed so that the web client does not return any errors. Hosts 127.0.0.1, localhost, and system hostname will automatically be added to the certificate.
- Login:
- Logo: The selected logo will be displayed in the login view. If no logo is chosen, a default one will be loaded.
- Text: Defines the informational message shown on the WebVision login page (pre-authentication). The content is written in Markdown and is intended to provide users with helpful context before signing in, such as support contacts, documentation links, maintenance notices, or policy reminders.
.gif) Note:This feature is available from N3uron version 1.22.0.
Note:This feature is available from N3uron version 1.22.0.
Installing the digital certificate on your browser
When accessing Web Vision using HTTPS, the web browser may display a security warning to notify users that the digital certificate is not recognized as valid. In order to avoid this message, the digital certificate can be imported and installed on the client's machine.
- Include the certified hosts (all urls, domains, and IP addresses used to access Web Vision from other systems). Localhost and 127.0.0.1 are included by default.
- Save the new settings by selecting “restart the module” when prompted.
- Export the certificate by clicking the button to the right of the HTTPS entry on the configuration settings tree.
- Install the certificate in the web browser to the Trusted Root Certification Authorities group. More information available in the appendix.