Introduction
This document aims to provide a comprehensive guide for system integrators and IT teams to securely provision and configure a N3uron deployment. It includes configuration recommendations for both the operating system and hardware, as well as specific guidelines for securing N3uron’s modules.
We recommend reviewing this guide before deploying N3uron in production environments, as the steps and recommendations may need to be adjusted to meet specific security requirements and regulations.
Hardware and Operating System
This section covers hardware and OS configurations to establish a robust security foundation for the system.
Trusted Platform Module (TPM)
N3uron should be deployed on hardware equipped with a Trusted Platform Module (TPM), a security chip that securely stores encryption keys, verifies firmware integrity, and ensures OS integrity during boot to prevent tampering.
Unified Extensible Firmware Interface (UEFI)
The system should use the modern UEFI (Unified Extensible Firmware Interface) instead of the legacy BIOS system. UEFI supports advanced security features like Secure Boot, which are critical to ensuring the trust and integrity of the system.
Secure Boot
Secure Boot should be enabled in the operating system to prevent malicious software from loading during the boot process. It also ensures the integrity of the OS by verifying that no authorized changes have been made. Refer to the official documentation of your operating system for detailed steps on configuring and enabling Secure Boot.
Full-Disk Encryption
Nodes running N3uron should be configured with full disk encryption at the operating system level to safeguard data and confidential information against unauthorized physical access.
For Windows systems, use the built-in Bitlocker security feature to encrypt disks and data volumes.
For Linux systems, the recommended method is to configure the Linux Unified Key Setup (LUKS) for disk encryption. Some custom Linux-based operating systems (eg. BalenaOS) support full disk encryption out-of-the-box.
For deployments in cloud environments, ensure that disk encryption is enabled using the cloud provider’s native tools (e.g., AWS KMS, Azure Disk Encryption).
Secure Access
The first step in securing a N3uron node is to ensure that communications with the Web User Interface (WebUI) are trusted and encrypted using HTTPS.
SSL/TLS
Note
The same configuration should also be applied to Web Vision instances.
Users must configure and enforce HTTPS in the N3uron WebUI using a trusted certificate signed by a public Certificate Authority (CA), an internal corporate CA, or a self-signed certificate generated by N3uron (not recommended for production environments).
.png)
Use the certificate helper to generate a Certificate Signing Request (CSR) for the node or a self-signed certificate.
.png)
Or load an existing TLS certificate into N3uron.
.png)
Remote Access
The N3uron Web User Interface (WebUI) should not be accessible from the public Internet without appropriate restrictions. Access to the WebUI should be limited to specific IP addresses and secured through a corporate Virtual Private Network (VPN) or a Zero Trust Network Access (ZTNA) solution.
To remotely access N3uron nodes, our Fleet Manager service provides a simple, secure, and firewall-friendly solution. It enables operators and IT teams to manage their fleet of N3uron nodes worldwide without exposing them to the public Internet or requiring the setup of complex VPN networks.
Note
Access through the Fleet Manager module requires N3uron to be running, which may present challenges during software updates or troubleshooting. Therefore, it is essential to maintain an emergency access mechanism for each node.
Identity and Access Management (IAM)
Access and control management in N3uron is based on four simple concepts: users, roles, permissions, and resources.
Resource: A resource refers to any object or entity in the platform that users can interact with. Examples of resources include tags, APIs, WebUI sections, and Web Vision screens.
Permission: A permission specifies an action that can be performed on a resource, such as read or write.
User: A user represents a uniquely identifiable entity—such as a person, system, or application—that is granted credentials to authenticate and access resources on the platform. Each user has a username, a password, and may optionally be assigned roles.
Role: A role is a set of permissions that define the scope of actions a user can perform. Each role has a name and optionally a description.
Note
In N3uron, permissions are always configured for roles, not individual users.
To implement a secure and effective Role-Based Access Control (RBAC) mechanism in N3uron, system administrators should adhere to the principles of Least Privilege and Separation of Duties. This involves granting each user the minimum access necessary to perform their tasks.
Default Passwords
When N3uron is installed, two built-in users are included by default:
admin: This user has unrestricted read/write access to the node.
user: This user has read-only access to view data and configuration.
Note
After installing N3uron, you MUST change the default passwords.
Go to Config→Users/Groups and select the admin user, then set a new password and click on Save.
.png)
Follow the same steps to change the user password and disable the user if it is not needed.
.png)
Active Directory (LDAP)
N3uron supports the Lightweight directory access protocol (LDAP) for centralized user management and authentication. The N3uron implementation of LDAP is compatible with the Microsoft Active Directory, OpenLDAP, FreeIPA and other cloud-based LDAP services. For reference see the N3uron LDAP configuration.
To securely integrate N3uron with LDAP configure the following settings:
Enable TLS for secure conectivity with the Active Directory server.
Configure a Certificate Authority (CA) to validate the server certificate.
Set Reject unauthorized to Yes.
Role-Based Access Control
The WebUI, Web Vision, REST API Server, and OPC UA Server modules support RBAC configuration in their Access section. This allows the assignment or revocation of role-based permissions to restrict access to module functionalities and the data model.
WebUI: Restrict login access to the Web User Interface and configure read/write permissions for each WebUI section.
Web Vision: Limit access to the Designer, the HMI/SCADA application, and the data model.
REST API Server: Configure role and token authentication, allowing fine-grained control over API calls and access to the data model.
OPC UA Server: Restric authentication access, node and tag permissions (browse, read, write, etc.) and limit access to the data model.
Modules
This section provides recommendations and best practices to securely configure specific N3uron modules.
Historian
The Historian module supports user authentication using SCRAM and TLS encryption to connect with an external MongoDB database. For guidance on securely configuring MongoDB please see the official Security Checklist.
Here are the recommended settings for Historian:
Enable and use Authentication against the database.
Enable TLS to encrypt traffic to the database.
Configure a Certificate Authority (CA) to validate the server certificate (Optional).
Set Reject unauthorized to Yes.
OPC UA
N3uron OPC UA modules (both client and server) implement the Sign&Encrypt security mode of the OPC UA protocol, authorization and trust using x509 certificates, and authentication with username/password.
Use the Sign&Encrypt security mode.
Use the Basic256&SHA256 security policy.
Enable user authentication with limited permissions and a strong password.
Disable anonymous logins to prevent unauthorized access.
Restrict access to resources in the server using role-based access control.
SQL
The N3uron SQL Client supports MySQL, MariaDB, SQL Server, PostgreSQL, OracleDB and TimescaleDB. Please refer to the official documentation of each database for proper security configuration.
Here are the recommended settings for SQL Client:
Enable SSL/TLS to encrypt traffic to the database.
Set Reject unauthorized to Yes.
For the strongest security use x509 client certificates.
Always enable authentication with the database, do not allow anonymous access.
Avoid using legacy or deprecated authentication methods.
MQTT and Sparkplug
The MQTT Client and Sparkplug Client modules support TLS encryption to secure communications with the MQTT broker, along with strong authentication using x509 certificates, JSON Web Token (JWT), and username/password.
Recommended settings to configure MQTT in N3uron:
Always use the TLS-secured MQTTS protocol.
Set Reject unauthorized to Yes.
Enable authentication to the MQTT broker, preferably using x509 certificates instead of passwords.
Use TagFilters to restrict the data model being published.
REST API
The REST API Server module supports TLS encryption using HTTPS, role-based and token-based access control, as well as fine-grained permissions for the N3uron API and the data model.
Enable and configure HTTPS, using a trusted certificate signed by a Certificate Authority instead of a self-signed certificate.
Disable unencrypted HTTP access, allowing access only through HTTPS.
Configure permissions in the Access section to restrict read and write access to the API.
Use TagFilters to limit access to the data model.
Data Diode
The Data Diode module enables one-way data transmission between two nodes in high-security IT-OT networks that do not allow bidirectional information flow. It supports AES-256-GCM symmetric encryption for data in transit, which must be enabled and configured with the same encryption key on both the sender and receiver.
WebUI and Web Vision
The WebUI and Web Vision modules supports secure access using TLS, role-based access control, and user authentication.
Enable and configure HTTPS, using a trusted certificate signed by a Certificate Authority instead of a self-signed certificate.
Disable unencrypted HTTP access, allowing access only through HTTPS.
Create a unique N3uron user for each operator accessing the node.
Configure role-based permissions to restrict access to the web Designer and Viewer in the Access section.
Use TagFilters to limit access to the data model.
Configure the security headers X-Frame-Options, X-Content-Type-Options, and Content-Security-Policy.
Links
N3uron Links provide secure connectivity and bidirectional data exchange between N3uron nodes. They use TLS 1.3 encryption to protect data in transit and employ certificates as an authentication mechanism (mTLS).
To securely configure Links:
Listen on the appropriate Network interface to reduce exposure.
Set Remote version support to TLS 1.3 & Node certificate
Ensure Trust all certificates and Accept expired certificates are disabled.
Manually configure Specific nodes for each incoming connection, do not allow connections of unknown nodes.
Restrict the data model to be published using Views.
Enable Store & Forward to prevent data loss.
Review and accept the certificates on each node.
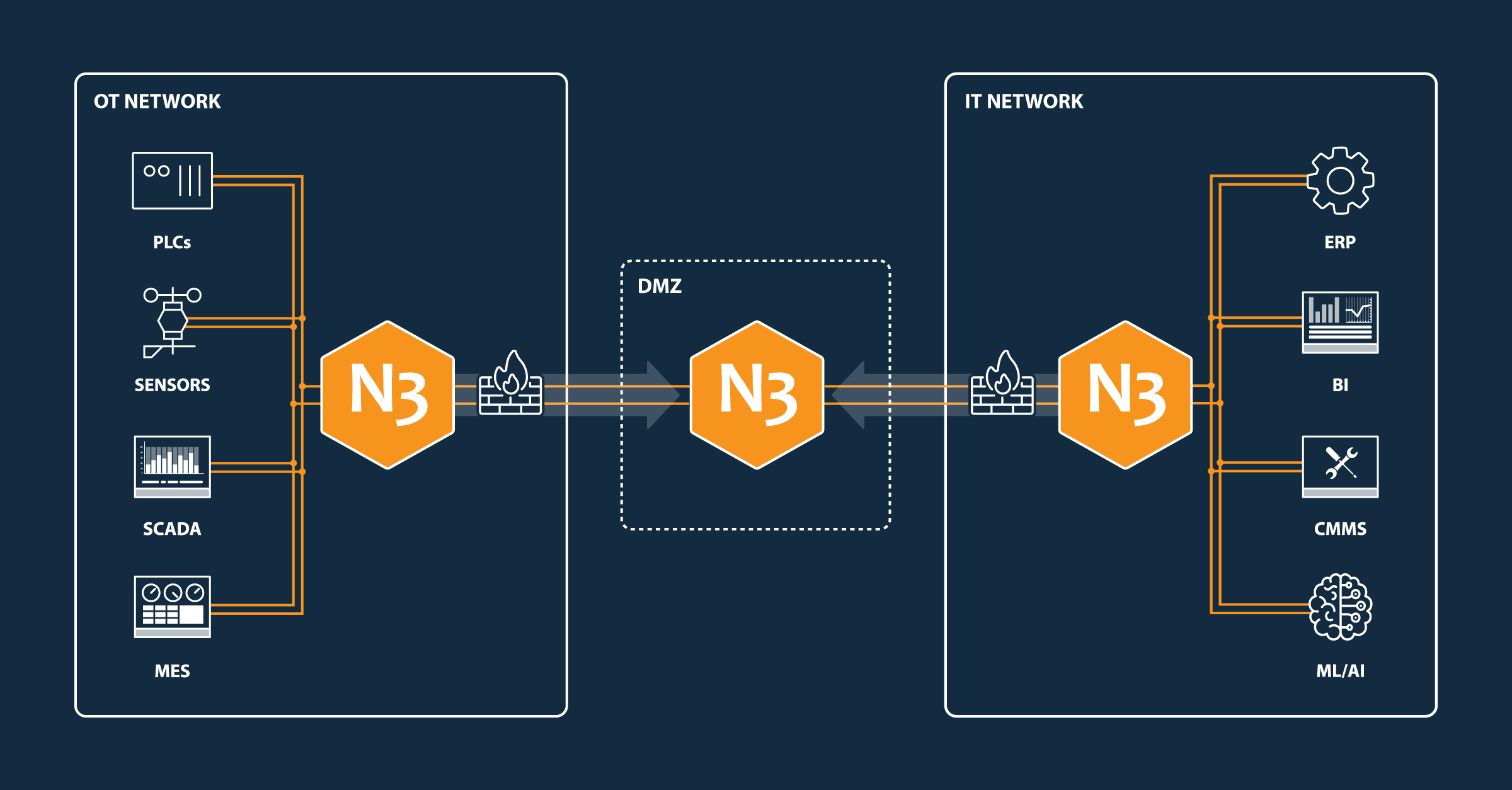
DMZ
N3uron Links can be deployed to create a demilitarized zone (DMZ) to securely segregate networks. This deployment typically requires:
A N3uron node deployed within the OT network (behind a restrictive firewall) configured to establish an outbound Link connection (OT → DMZ) to the N3uron node in the DMZ.
A N3uron node in the DMZ that only accepts inbound connections and is restricted from initiating outbound connections.
A N3uron node in the IT network (behind the corporate firewall) that establishes an outbound connection to the N3uron node in the DMZ (DMZ ← IT).
Due to the bidirectional nature of N3uron Links, both the OT and IT nodes can securely exchange data through the DMZ.
Logging and Auditing
Logging and auditing are critical components of any robust security strategy. They provide the foundation for detecting, understanding, and responding to security incidents, as well as maintaining regulatory compliance and accountability.
Logs
Each module includes a Logger configuration that allows to specify the log level and retention period. By default, the retention period is set to 7 days, and logs older than this are automatically deleted. To comply with security standards or regulatory requirements, you should extend the retention period to several months.
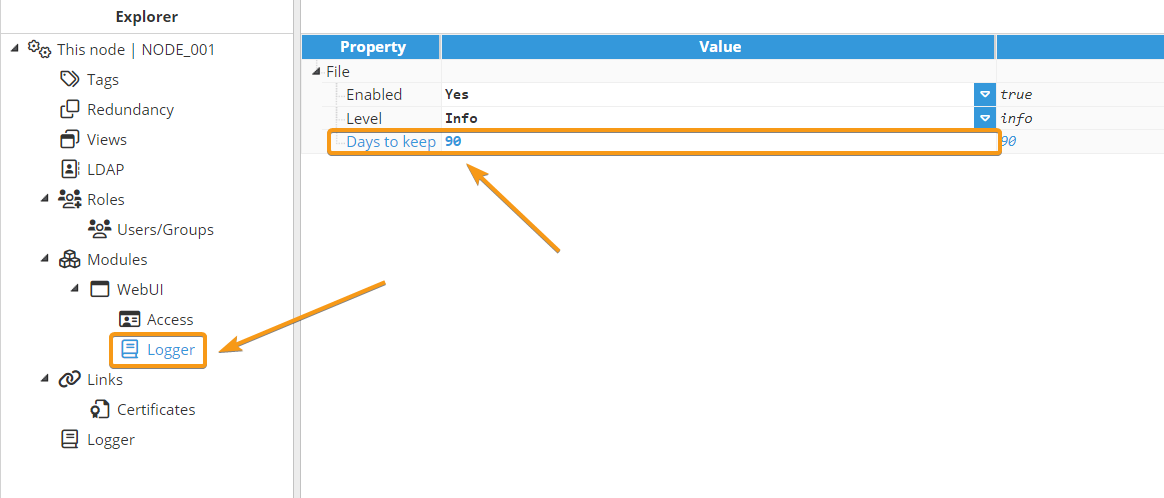
The N3uron logs for each module are located in the /opt/n3uron/log/<ModuleName> folder in Linux systems or C:/Program Files/N3uron/log/<ModuleName> folder in Windows, a new file is created each day.
Key security logs include:
Login and access logs for the WebUI module.
Login and access logs for the Web Vision module.
Logs from modules that allow remote read/write access: REST API Server, OPC UA Server, Modbus Server, DNP Server, etc
N3uron logs are stored in a plain log format, allowing seamless integration with log forwarders to continuously send logs to a centralized Security Information and Event Management (SIEM) system.
Audit Trail
The Audit Trail module provides a detailed record of activities within the node, such as tag writes, module status changes, configuration changes, and licensing modifications.
By default, the Audit Trail module retains logs for 30 days. Extend the retention period as needed to meet security and regulatory requirements.
.png)
Security operators can visualize activities and generate reports using the Audit Trail Display.
Node Decommissioning
When decommissioning a N3uron node, follow these steps to prevent unauthorized access, mitigate data leakage, and ensure compliance with regulatory standards.
Unlicense the node
Note
Migrating a license to a new node requires an active Support and Maintenance (S&M) contract for that specific license. Please see our S&M details at Pricing.
Unlicensing a node allows you to recover and reuse an existing N3uron license. Otherwise, the license will be lost.
To unlicense a node go to Licensing and click on Unlicense. For more details about recovering a license, refer to Licensing.
.png)
Revoke access keys
Any secrets, passwords, access keys, API keys, x509 certificates, or other credentials used by the node to access external systems should be revoked to prevent unauthorized access
Note
Using full disk encryption is recommended to safeguard any residual secrets remaining on the node. For more information, refer to the Encryption at rest section in this guide.
Uninstall N3uron
For Windows systems: Refer to Uninstall N3uron in Windows.
For Linux systems: Refer to Uninstall N3uron in Linux.